Hub Authentication Module
The Hub authentication module is the default authorization scheme for managing user account credentials. This module is built into your Hub installation and enabled by default.
The settings of this authentication module let you control how user manage their Hub credentials.
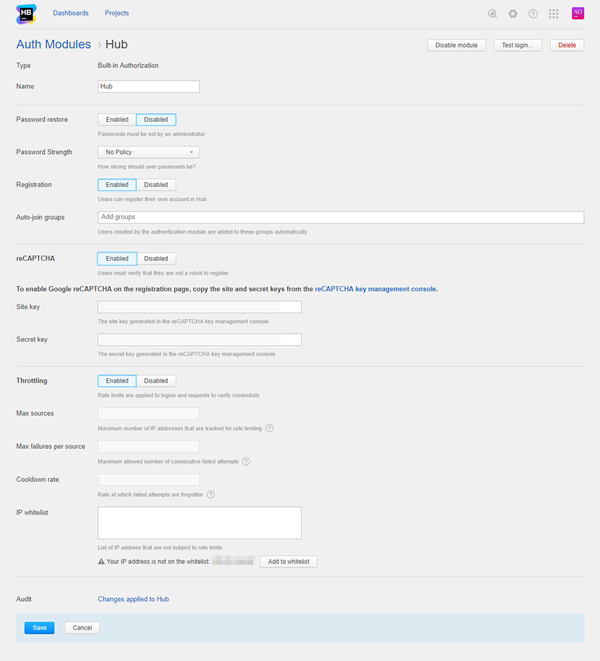
General Settings
The settings are configured automatically when you install Hub.
| Setting | Description |
|---|---|
| Type | Displays the type of service that is enabled for authentication in Hub. Built-in Authorization means that this module is a part of Hub and is not installed separately. |
| Name | Stores the name of the authentication module. Use this setting to distinguish this module from other authentication modules in the Auth Modules list. |
| Password Restore | Enables the option for users to reset a forgotten password. When enabled, Hub sends an email message with a link to restore their password to users who request a password reset. |
| Password Strength | Stores the password policy setting applied to Hub accounts. For more information about password strength and security, see Set a Password Policy. |
| Registration | Enables the creation of accounts for users who register themselves in Hub. If you disable this option, only users with existing Hub accounts are able to log in. When enabled, additional settings that you can use to manage users who register their own accounts in Hub are shown. For a detailed description of these settings, see Registration Settings. |
| Throttling | Enables rate limitation for logins and requests to verify credentials. When enabled, the settings that determine how throttling is applied are shown. For a detailed description of these settings, see Throttling Settings. |
| Audit | Links to the Audit Events page in Hub. There, you can view a list of changes that were applied to this authentication module. |
Registration Settings
When the Registration option is enabled, there are additional settings that you can use to manage users who register their own accounts in Hub.
| Setting | Description |
|---|---|
| Registration | Enables the creation of accounts for users who register themselves in Hub. If you disable this option, only users with existing Hub accounts are able to log in. |
| Auto-join Groups | Automatically adds new users to groups when they register their own accounts in to Hub. You can select one or more groups. New users that auto-join a group inherit all of the permissions that are assigned to this group. We recommend that you add users to at least one group. Otherwise, new users are only granted the permissions that are currently assigned to the All Users group. Do not use this option to add users to groups that grant unnecessary access to sensitive data. |
| reCAPTCHA | Enables the use of reCAPTCHA on the registration page. This feature protects your installation from registration bots. When you enable this option, you need to register Hub in the Google reCAPTCHA key management console. Follow the instructions below to activate this feature. |
To enable reCAPTCHA on the registration page:
- Set the reCAPTCHA option to Enabled.
- Additional settings for the reCAPTCHA setup are shown.
- Click the link to access the reCAPTCHA key management console.
- The Create reCAPTCHA key page opens.
- Register your Hub domain with the reCAPTCHA service. reCAPTCHA is a part of Google services, so you can use your Google account to log in. Read the tips provided on the page before you register and generate your keys.
- Copy the Site key in Google and paste it into the corresponding input field in the Hub authentication module.
- Copy the Secret key in Google and paste it into the corresponding input field in the Hub authentication module.
- Click the Save button.
- The reCAPTCHA validation input is enabled for users who register their own accounts in Hub.
Throttling Settings
The throttling settings let you apply rate limits to sources of multiple consecutive failed authentication requests. This feature helps protect the application from brute-force attacks. For more information about this feature, see Throttle Failed Logins.
When the Throttling option is enabled, there are additional settings that manage how throttling is applied to logins and requests to verify credentials.
The only setting that you can update directly in the user interface is the IP whitelist. All of the other settings are displayed in read-only mode.
You can specify new values for each of these parameters when you start the Hub service. For instructions, see List of System Properties.
| Setting | Description | Parameter |
|---|---|---|
| Throttling | Enables rate limitation for logins and requests to verify credentials. | jetbrains.hub.auth.login.throttling.enabled |
| Max sources | The maximum number of IP addresses that are tracked for rate limiting. The purpose of this setting is to maintain a relative large number of counters that is not an infinite value. | jetbrains.hub.auth.login.throttling.size |
| Max failures per source | The maximum number of consecutive failed requests that are allowed before rate limitations are applied to incoming requests from the tracked IP address. | jetbrains.hub.auth.login.throttling.failures |
| Cooldown rate (count) | The number of entries that are removed from the counter for each IP address at the interval that is shown. | jetbrains.hub.auth.login.throttling.cooldown-value |
| Cooldown rate (interval) | The interval at which entries are removed from the counter for each IP address, in seconds. | jetbrains.hub.auth.login.throttling.cooldown-period-sec |
| IP whitelist | A list of IP addresses that are not tracked for failed login requests. Enter each IP address on a new line. When you specify the value for this parameter as a JVM option, use a comma-separated list. IPv4 and IPv6 are both supported. Subnet masks are not supported. A warning is displayed to users who have the Update Auth Module permission when they access the page from an IP address that is not already on the whitelist. It is always important for an administrator to be able to log in to the application, even when throttling is active. To add your current IP address, click the Add to whitelist button. | jetbrains.hub.auth.login.throttling.white-list |