Google Auth Module
This authentication module lets users log in to Hub with the email addresses and passwords they manage in Google.
When you enable Google authentication in Hub:
Your users log in to Hub with the credentials they use for their Google accounts.
Your Hub users have fewer accounts and passwords to remember.
New users with Google accounts can create their own accounts in Hub.
Enable Google Authentication
To allow users with existing Google accounts to log in to Hub, enable the Google authentication module.
This procedure takes place in three steps:
Generate a Redirect URI in Hub. When you create an authentication module for Google, Hub generates a redirect URI to use with this service. This URI identifies the source of each login request to Google.
Generate a Client ID and Secret in the Google API Manager. Every login request sent from Hub to Google includes a unique identifier. The ID and secret you store in the authentication module tell Google that each login request is authorized.
Enable the Auth Module in Hub. When you have generated the information Hub uses to authenticate with Google, copy the values into Hub and enable the module.
Generate a Redirect URI in Hub
To get started, open YouTrack and create an authentication module for Google accounts. When you create the authentication module, YouTrack generates a redirect URI to use with the authorization service.
To generate a redirect URI in Hub:
In the Access Management section of the Administration menu, select .
- From the Add Module drop-down list, select Google.
The Auth Modules page displays the settings for a new Google authentication module.
Hub generates a redirect URI for you to use in Google.
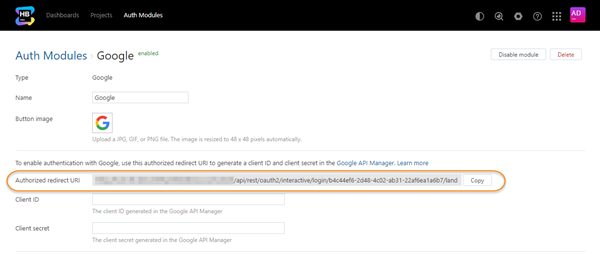
Copy the redirect URI as instructed on the page.
- Click the link to access the Google API Manager.
Generate a Client ID and Secret in the Google API Manager
Log in to your Google account.
Select or create a project.
Open the API Manager.
On the left, select Credentials.
- From the Create credentials drop-down list, select OAuth client ID.
The Create client ID page opens.
Click the Configure consent screen button.
- In the OAuth consent screen page, enter a product name and click the Save button.
You are redirected to the Create client ID page.
- For the Application type, select Web application.
Additional input fields for defining the client ID are shown.
In the Authorized redirect URIs field, paste the redirect URI you copied from the Auth Module page in Hub.
- Click the Create button.
Google generates the credentials you need to set up the Hub module and displays them in a pop-up window.
Enable the Auth Module in Hub
Copy the client ID from Google and paste it into the Client ID input field in Hub.
Copy the client secret from Google and paste it into the Client Secret input field in Hub.
Configure the optional settings for the authentication module. For more information, see the Optional Settings section.
- Click the Enable module button.
The Google authentication module is enabled.
The icon stored in the Button Image setting is added to the login dialog window. Users can click this icon to authenticate with their Google accounts.

Settings
Field | Description |
|---|---|
Type | Displays the name of the application or service that is enabled for third-party authentication in Hub. |
Name | Stores the name of the authentication module. Use this setting to distinguish this module from other authentication modules in the Auth Modules list. The name is also shown in the tooltip for the third-party service icon on the login form. |
Button Image | Displays the image used for the button that a user clicks to log in to Hub with a Google account. |
Authorized redirect URI | Displays the redirect URI that is used to register the connection to Hub in Google. |
Server URL | Displays the URL of the server to which Hub sends a login request when a user logs in with a Google account. |
Client ID | Stores the identifier Google uses to validate a login request. You generate this value in the Google API Manager when you configure the authorization settings for a web application and enter an authorized redirect URI. |
Client Secret | Stores the secret or password used to validate the client ID. You generate this value in the Google API Manager together with the client ID. |
Additional Settings
The following options are located at the bottom of the page. Use these settings to manage Hub account creation and group membership, and to reduce the loss of processing resources consumed by idle connections.
Option | Description |
|---|---|
User creation | Enables creation of Hub accounts for unregistered users who log in with an account that is stored in the connected authorization service. Hub uses the email address to determine whether the user has an existing account. |
Restrict Domain | Restricts the creation of user accounts to users with an email address from the specified domain. This option is only active when you enable the Create Users option. |
Auto-join groups | Adds users to a group when they log in with an account that is stored in the connected authorization service. You can select one or more groups. New users that auto-join a group inherit all of the permissions assigned to this group. |
Connection timeout | Sets the period of time to wait to establish a connection to the authorization service. The default setting is 5000 milliseconds (5 seconds). |
Read timeout | Sets the period of time to wait to read and retrieve user profile data from the authorization service. The default setting is 5000 milliseconds (5 seconds). |
Audit | Links to the Audit Events page in Hub. There, you can view a list of changes that were applied to this authentication module. |