Require Two-factor Authentication
The Two-factor authentication setting in the group profile lets administrators require two-factor authentication (2FA) for any group in Hub.
When enabled, group members are required to set up two-factor authentication (2FA) for their Hub accounts. Access rights for members of this group who have not enabled 2FA are restricted. Once a user has enabled 2FA, the access rights that are granted to their account are restored.
When disabled, group members are not required to set up 2FA for their Hub accounts. Users may still choose to enable this security feature on their own.
You can use this feature to improve the security of your Hub installation and the applications that are connected to it. If you want everyone who connects to your installation to use 2FA, enable this feature for the All Users group. You can enable the feature for a dedicated group and add only users who have access to sensitive information.
When you enable this feature for a group in Hub, all of its members are immediately required to set up 2FA for their Hub accounts. Members of the group who have not already enabled 2FA for their Hub accounts are prompted to do so the next time they log in. Users can dismiss the notification and cancel 2FA setup, however, their access to Hub and connected services will be severely restricted. To remove this restriction and resume working with the permissions that are available to their accounts, they must add a second authentication factor to their accounts.
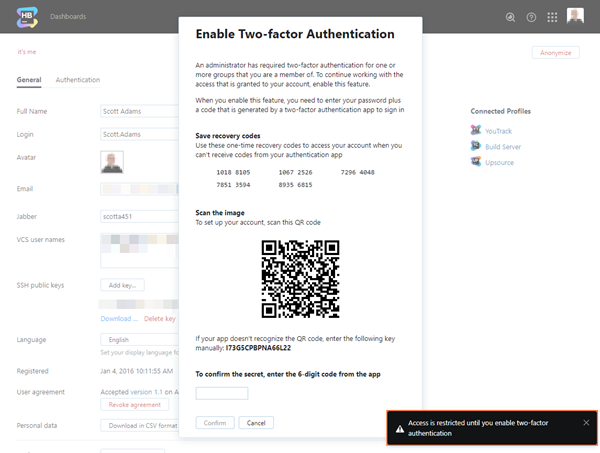
Users who set up 2FA for their own accounts may require advanced preparation. If, for example, your organization doesn't provide users with hardware tokens, users may need to download an authentication app or register with a third-party authentication service. Users who only have credentials that are managed in third-party authentication providers like Google or GitHub will need to add Hub credentials to their accounts.
Before you require 2FA for a group, take a few precautions to make sure you don't block users unnecessarily:
Notify users that their logins will require a second authentication factor in the near future. Share a link to the pages that provide instructions for setup. To meet the requirement, users can choose between app-based and token-based authentication factors.
Review the list of limitations that apply to this feature and be prepared to answer questions from users. For details, see Limitations.
Identify users who haven't enabled 2FA before you require the feature for a specific group. When applied as a filter to the Users page, the following search query returns a list of users who have not enabled 2FA:
not has: 2FAYou can further refine the search by limiting the results to members of a specific group:
in: <group name> and not has: 2FAYou can also see if there are any members in a group whose credentials don't support two-factor authentication:
in: <group name> and not is: supporting2FAOnce you have verified that every member of the group has enabled 2FA, you can require the feature without disrupting their work.
To require 2FA for group members:
From the Access Management section of the Administration menu, select Groups.
Click the name of the group for which you want to require 2FA. Use the filter in the page header to find a group by name, project, or another supported attribute.
On the group profile page, click the Settings tab.
For the Two-factor authentication setting, click the Required button.
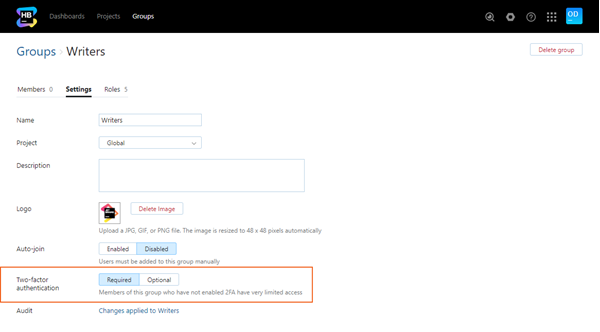
Click the Save button.
Members of the group who have not already enabled 2FA for their Hub accounts are prompted to do so the next time they log in. Access is restricted until they enable a second authentication factor.
A 2FA badge is added to the right of the group name on the Groups page.