LDAP Authentication Module
An LDAP authentication module lets users log in to YouTrack and any connected services with credentials that are stored in a directory service.
- Background Information
- Enable LDAP Authentication
- Test the Connection to your Directory Service
- Settings
- LDAP Attributes
- Auto-join Groups
- Sample Configurations
Background Information
An LDAP integration does not import all of the user accounts from the directory service. YouTrack only creates a user account when an unregistered user first logs in to YouTrack or a connected service.
When LDAP authentication is enabled, YouTrack checks the directory service for each login attempt. Users who have been removed from the directory service cannot log in to YouTrack.
YouTrack provides pre-configured authentication modules for LDAP, OpenLDAP, and Active Directory. You can configure a module to use the standard LDAP scheme or LDAPS over SSL.
Enable LDAP Authentication
To allow users stored in a directory service to log in to YouTrack, enable an LDAP authentication module.
Prerequisites
Before you start, verify the following requirements:
- You have Create Auth Module and Update Auth Module permissions in YouTrack.
- If you want to authenticate over SSL, you have imported the SSL certificate for your LDAP server. For more information, see SSL Certificates.
Instructions
To enable the module, follow these steps.
- In the Access Management section of the Administration menu, select Auth Modules.
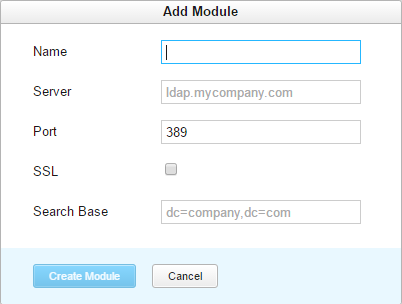
- From the Add Module drop-down list, select the option that corresponds to the directory service you want to enable. You can select LDAP, OpenLDAP, or Active Directory.
- In the Add Module dialog, enter values for the following settings:
- Click the Create Module button.
- The LDAP authentication module is enabled.
- The Auth Modules page displays the settings for the LDAP authentication module. The module is pre-configured with standard settings that are based on the information you provided in the Add Module dialog. For additional information about the settings on this page, see Settings.
Test the Connection to your Directory Service
To verify that the LDAP authentication module is connected to your directory service, test the connection.
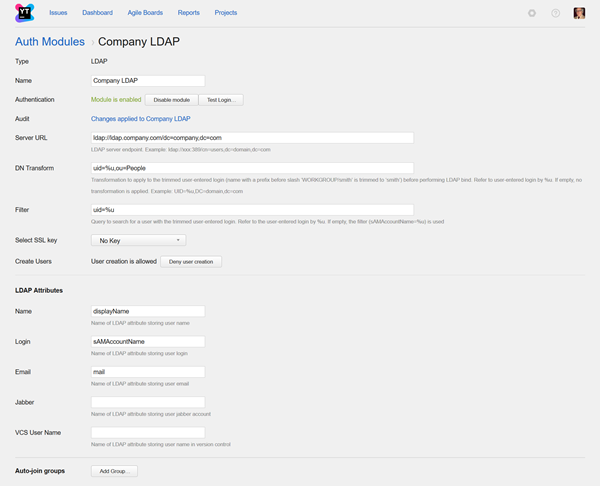
Settings
Use the following settings to configure how YouTrack connects to your directory service.
| Field | Description | Additional Information |
|---|---|---|
| Type | Displays the name of the application or service that is enabled for third-party authentication in YouTrack. | |
| Name | Stores the name of the authentication module. Use this setting to distinguish this module from other authentication modules in the Auth Modules list. | |
| Authentication | Displays the current status of the module. This status indicates whether the module is currently enabled or disabled. | |
| Audit | Links to the Audit Events page in YouTrack. There, you can view a list of changes that were applied to this authentication module. | |
| Server URL | Stores the LDAP URL of the directory service used to authenticate a login request in YouTrack. | The LDAP URL uses the format ldap://host:port/DN. Enter the full distinguished name (DN) of the directory where user accounts are stored. |
| Bind DN | Stores the query used to bind with the directory service. This query looks up the distinguished name of the user to be authenticated. The username is referenced with an expression. The expression maps a substitution variable to the attribute that stores the username in the directory service. The attribute you select determines which query is used in the filter string. | The value entered as the username on the login page is trimmed before it replaces the substitution variable.
If the user specifies a domain, it is discarded. For example, a username with the value WORKGROUP\smith is trimmed to smith.
To specify a domain, enter the domain name as a static value. For example, WORKGROUP\%u. |
| Filter | Stores the expression used to filter for a specific user. The substitution variable in the expression is replaced with the value entered as the username on the login page. | The value entered in this field locates the authenticated user in the directory service. |
| SSL Key | Selects the keystore that contains the private key for your YouTrack server. | Use this setting when your LDAP service requires a trusted certificate to establish a connection to another service. This list displays only keystores that have been imported into YouTrack. For more information, see SSL Keystores. |
| Create Users | Enables creation of YouTrack accounts for unregistered users who log in with an account that is stored in the connected directory service. YouTrack uses the email address to determine whether the user has an existing account. | All LDAP authentication modules must allow user creation. If user creation is denied, unregistered users are shown an error. |
LDAP Attributes
Use the following settings to map attributes stored in your directory service to user accounts in YouTrack.
Auto-join Groups
Use this setting to add users to a group when they log in with an account that is stored in the connected directory service.
You can select one or more groups.
New users that auto-join a group inherit all of the permissions assigned to this group.
We recommend that you add users to at least one group.
Otherwise, a new user is only granted the permissions that are currently assigned to the All Users group.